See what ports are open on the RPi
netstat -lptn
or the long version is:
netstat --listening --programs --tcp --numeric
In Part 1 I discussed the technologies that make up the Blocks themselves, adding a block to the end of the chain and handle the distribution of the final BlockChain. Now we can consider how we protect each block in the chain and how we can ensure that the chain stays unbroken.
We have a new block with the contents all secured and consensus has agreed that this block will be added to the end of the chain. What is to stop someone from removing a previously created block from the chain and replacing it with something else?
If we calculate the hash of the contents of the previous block we can then use this ‘signature hash’ value as part of the process of adding the new block on the end of the chain.
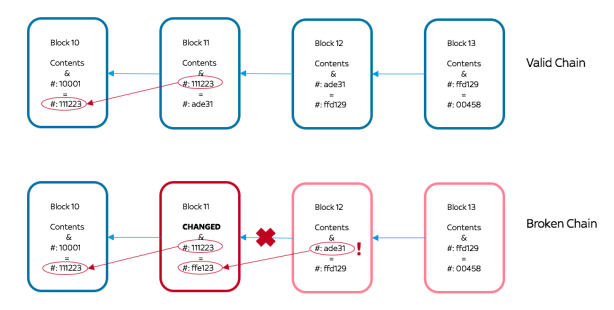
If the contents of a block is changed, the ‘signature hash’ will be different from the one stored in the next block of the chain and everyone will know that it has been changed. Consensus ensures that only consistent chains exist and that broken chains get dropped.
We’ve shown that the BlockChain won’t allow alterations to existing blocks, how could we add a false block to the end?
Smart Contracts are the next iteration of the original BlockChain concept.
They work on the idea of storing a small program within the BlockChain that can then run in its own virtual machine when required. When invoked this contract programme can then be used to validate, enforce and manage transactions between two or more parties in a trusted way without requiring the services of a middleman.
The outcome of this invocation can then be written back to the BlockChain or to local contract storage where it will remain.
While seen as the next big thing int an already big thing, Smart Contracts are still trying to establish themselves in real world use.
As they use ‘Turing Complete’ languages to define the contract they are vulnerable to poor coding or flaws in the underlying virtual machine. Development environments are still immature increasing the risks further.
Ethereum ‘lost’ ~$53 million because they built a VM and a language that had flaws that were exploited to make contracts do unexpected things, in this case transfer the holdings to another account within the Ethereum ecosystem.
N.B. This issue has since been rectified by basically rolling back to a point in the ledger prior to the loss and then forcing a fork in the BlockChain where the monies never left the DAO. This has caused a debate in that it proves that the BlockChain is not inviolate – if enough people say so, the BlockChain can be changed and more importantly there are no attempts to fix the underlying issues in the VM and language itself. So in theory this loss could be replicated again in the future.
BlockChain is the new must use buzzword in technology and it claims to provide the capability for building trust between disparate and non connected systems.
This post is based on the presentation I wrote to explain the potential of BlockChain for my employer.
So what is BlockChain, where did it come from and why the sudden interest?
The sudden interest comes from the fact that in theory a BlockChain allows for a trusted, accessible, permanent, encrypted, distributed record that is almost impossible to modify. It allows two parties to perform transactions without the need for a trusted third party – something that can add both costs and complexity to the original transaction.
BlockChain is being used for everything from currency and diamond registry through to medical record management and music rights control. Large scale schemes such as welfare payment control are being investigated by the UK government.
BlockChain is the underlying technology for a virtual currency called BitCoin. As a technology used for the manipulation of funds, it has to be transparent, reliable and secure. While BitCoin initially suffered from bad press relating to its association with criminal organisations (Silk Road) and the high profile failure of businesses (Mt Gox), it is now established as a true virtual currency.
At its most basic BlockChain is the combination of four current technologies in a new and unique way:
Public key encryption uses two keys to protect content.
One key is Private and is held ONLY by the user, the other key is Public and is available to everyone. These two keys are created together at the same time and are a mathematical pair – they will only work together.
If I want to send a message to someone, I use their public key to ‘sign’ the message. Signing the message effectively encrypts it so that only the private key can open it. Any attempt to change the message will change it and will result in the private key not opening it. The inability to open it implicitly implies tampering has occurred.
Software such as Pretty Good Privacy (PGP) made this incredibly complex topic easy for everyone to use, much to the horror of law enforcement agencies worldwide. At one point the PGP software was classed as a weapon and placed on a restricted list limiting it’s availability outside of the US!
Cryptographic hashing converts a value of variable length into an alphanumeric string of fixed length. Hashes are a ONE WAY function – you can’t take a hash and find out the original value. Hashes are also very quick to calculate with the ability to do so available in all programming languages.
The specific method of hashing used determines the length of the final hash output. SHA1, MD5 & SHA256 are all common hashing methods, each providing different levels of complexity and output size.
For example using SHA1 to hash a simple string:
Hello world => 7b502c3a1f48c8609ae212cdfb639dee39673f5e
Changing even the smallest thing (“H” to “h”) results in a completely different result!
hello world => 2aae6c35c94fcfb415dbe95f408b9ce91ee846ed
Hashing can be used in everything from password validation to ensuring the file you download has not beed altered by malicious third-parties.
Using Peer to peer technologies allows the BlockChain to be distributed across hundreds if not thousands of nodes.
A node can be a simple device making use of the BlockChain or a more complex or powerful device that is used to manage the BlockChain itself.
As only 4 nodes are required to ensure that the BlockChain remains available, accurate and up to date, the more nodes that host it serve only to increase reliability, speed and robustness.
Consensus is a technique in which a set of nodes can reach an agreed outcome without a designated leader and with automatic detection of tampering.
When a new block is proposed to the BlockChain, all nodes must add it to their own BlockChain. If any node tries to lie, that node becomes tainted. As long as there is no single party with the control of >= 51% of the nodes, the BlockChain is always up-to-date and truthful.
Quorum systems are applied in BlockChain to reduce the complexity of the consensus algorithms with no penalty in consistency, partitioning the nodes in a similar way to electoral constituencies.
Consensus must happen before a new block can be added to a chain, so the only way to add a ‘bad block’ to the chain is to control the majority of the nodes.
As the nodes are distributed throughout the internet, this becomes impractical and this means that we have established an effective trust between all the users of the BlockChain without requiring a third-party.
By combining these technologies we can create the next block for inclusion on a chain: